Solved Q2 Based On Data Encryption Standard Des If The Chegg Q2: based on data encryption standard (des), if the shared key is "computer" and the output of round 2 is “56 37 78 05 ab 55 34 81". find the output of round 1. (7 points) your solution’s ready to go! our expert help has broken down your problem into an easy to learn solution you can count on. Network security: data encryption standard solved questions topics discussed: 1. five solved examples based on the data encryption standard (des) .more.

Solved Q2 Based On Data Encryption Standard Des If The Chegg Lecture 4 data encryption standard (des) block ciphers map n bit plaintext blocks to n bit ciphertext blocks (n = block length). for n bit plaintext and ciphertext blocks and a fixed key, the encryption function is a bijection; e : p x k → c s.t. for all key k n n ∈ k, e(x, k) is an invertible mapping, written ek(x). In des, encryption or decryption uses 16 × 2 2 = 34 permutations, because each mixer uses two permutations and there are two permutations before and after the rounds. the round key generator uses 17 permutation operations: one parity drop and 16 compression permutation operations for each round. Def generate round keys(encryption key): round keys = [] key = encryption key.deep copy() for round count in range(16): [lkey, rkey] = key.divide into two() shift = shifts for round key gen[round count] lkey << shift rkey << shift key = lkey rkey round key = key.permute(key permutation 2) round keys.append(round key) return round keys. Des, as the first important block cipher, has gone through much scrutiny. among the attempted attacks, three are of interest: brute force, differential cryptanalysis, and linear cryptanalysis.

Solved Q2 Based On Data Encryption Standard Des If The Chegg Def generate round keys(encryption key): round keys = [] key = encryption key.deep copy() for round count in range(16): [lkey, rkey] = key.divide into two() shift = shifts for round key gen[round count] lkey << shift rkey << shift key = lkey rkey round key = key.permute(key permutation 2) round keys.append(round key) return round keys. Des, as the first important block cipher, has gone through much scrutiny. among the attempted attacks, three are of interest: brute force, differential cryptanalysis, and linear cryptanalysis. Data encryption standard is a 64 bit block cipher with five modes: electronic codebook (ecb) cipher block chaining (cbc) cipher feedback (cfb) output feedback (ofb) counter (ctr) all modes operate on 64 bits of plaintext to generate 64 bit blocks of ciphertext. the key that is used by des is 56 bits long. This set of cryptography multiple choice questions & answers (mcqs) focuses on “the data encryption standard (des) and it’s strength”. 1. des follows a) hash algorithm b) caesars cipher c) feistel cipher structure d) sp networks view answer 2. the des algorithm cipher system consists of rounds (iterations) each with a round. The symmetric key encryption algorithm, the data encryption standard (des), is widely known. it was created in the 1970s to protect sensitive information. des uses a 56 bit key and works on 64 bit blocks of data which means that it forms an integral component to initial cryptographic systems. Learn about data encryption standard (des) algorithm with its program implementation in c. data encryption standard is a symmetric key algorithm for the encrypting the data. it comes under block cipher algorithm which follows feistel structure. here is the block diagram of data encryption standard.
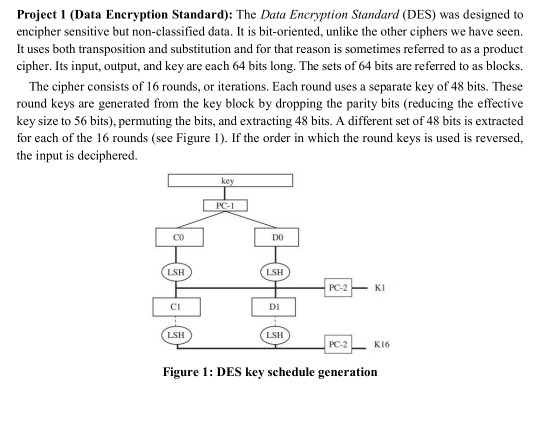
Solved Project 1 Data Encryption Standard The Data Chegg Data encryption standard is a 64 bit block cipher with five modes: electronic codebook (ecb) cipher block chaining (cbc) cipher feedback (cfb) output feedback (ofb) counter (ctr) all modes operate on 64 bits of plaintext to generate 64 bit blocks of ciphertext. the key that is used by des is 56 bits long. This set of cryptography multiple choice questions & answers (mcqs) focuses on “the data encryption standard (des) and it’s strength”. 1. des follows a) hash algorithm b) caesars cipher c) feistel cipher structure d) sp networks view answer 2. the des algorithm cipher system consists of rounds (iterations) each with a round. The symmetric key encryption algorithm, the data encryption standard (des), is widely known. it was created in the 1970s to protect sensitive information. des uses a 56 bit key and works on 64 bit blocks of data which means that it forms an integral component to initial cryptographic systems. Learn about data encryption standard (des) algorithm with its program implementation in c. data encryption standard is a symmetric key algorithm for the encrypting the data. it comes under block cipher algorithm which follows feistel structure. here is the block diagram of data encryption standard.
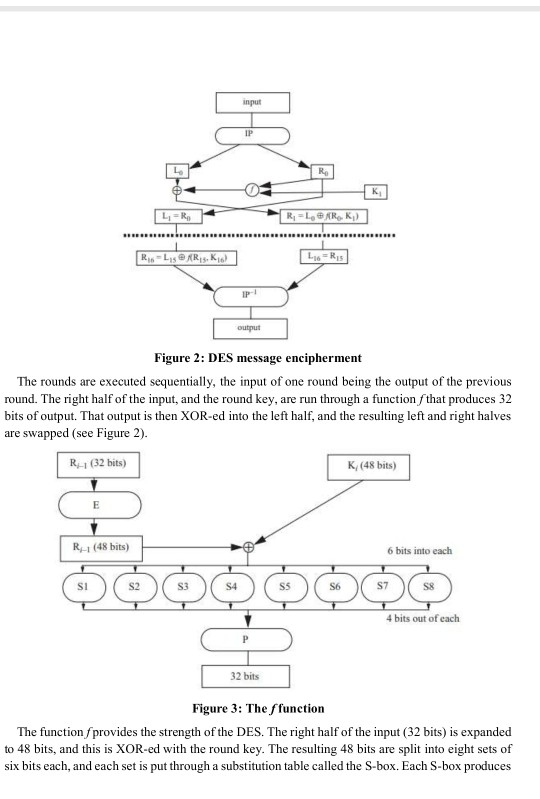
Solved Project 1 Data Encryption Standard The Data Chegg The symmetric key encryption algorithm, the data encryption standard (des), is widely known. it was created in the 1970s to protect sensitive information. des uses a 56 bit key and works on 64 bit blocks of data which means that it forms an integral component to initial cryptographic systems. Learn about data encryption standard (des) algorithm with its program implementation in c. data encryption standard is a symmetric key algorithm for the encrypting the data. it comes under block cipher algorithm which follows feistel structure. here is the block diagram of data encryption standard.