
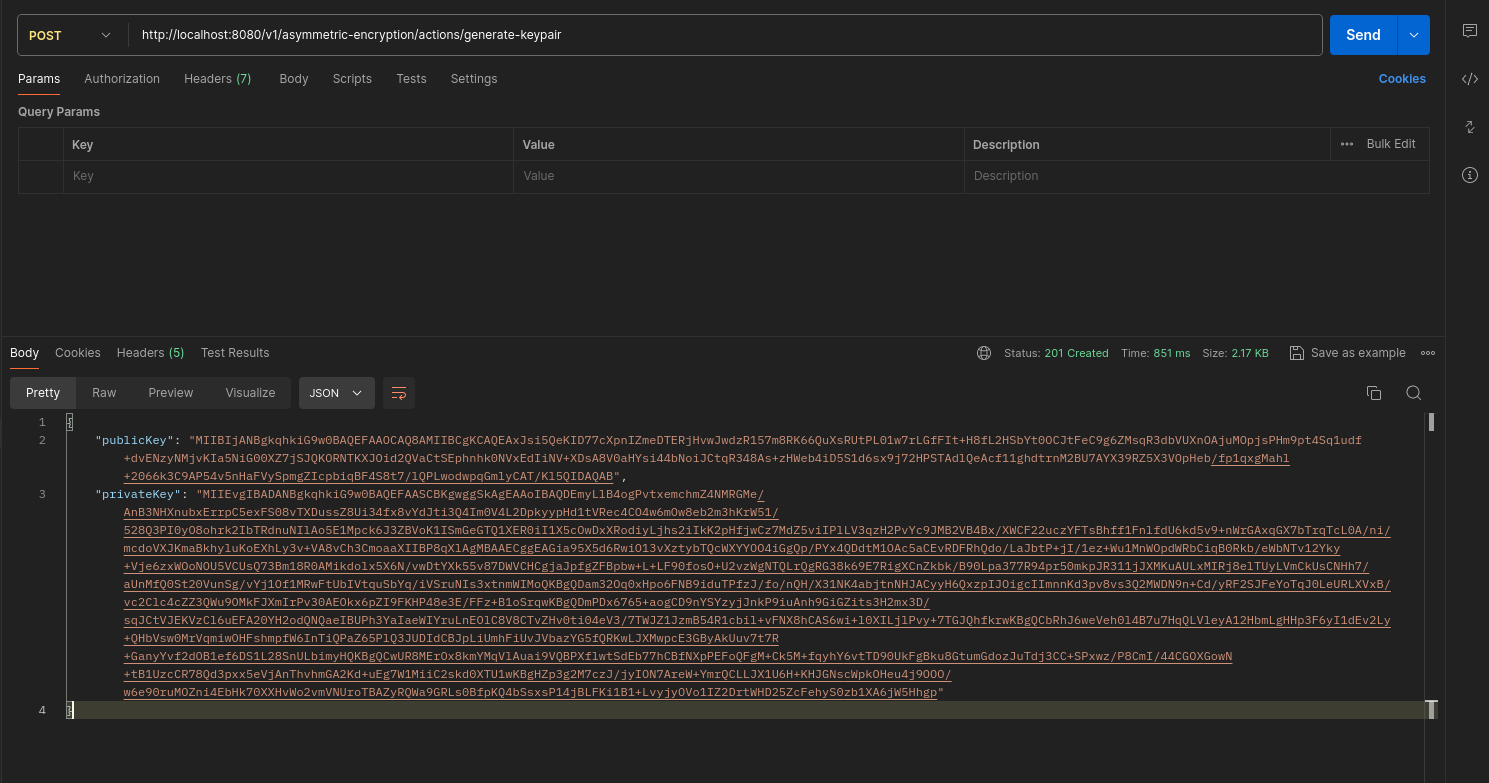
Symmetric Vs Asymmetric Encryption Which Is Better For Data Security This repository is a walkthrough on how to use spring security with jwt (asymmetric encryption) approach. to get you started you can simply clone the repository and install the dependencies. you need git to clone the repository. you will need at least: clone the repository using git: cd spring security jwt asymmetric encryption.git. The spring security crypto module provides support for symmetric encryption, key generation, and password encoding. the code is distributed as part of the core module but has no dependencies on any other spring security (or spring) code.
Asymmetric Encryption 2d Garden In this video, we’ll show you how to implement asymmetric encryption in your spring boot application using jwt tokens and private public key pairs. learn how. Asymmetric encryption (e.g., rsa with rs256) uses a private key to sign the jwt and a public key to verify it. the private key remains secure on the authentication server, while the public key can be freely shared with services that need to validate jwts. 1) does the asymmetric signing of jwt tokens support the issuing of refresh tokens? 2) why my authorization server is not issuing a refresh token based on the below configuration? @override. public void configure(authorizationserverendpointsconfigurer endpoints) throws exception { tokenenhancerchain chain=new tokenenhancerchain();. Learn how to convert a spring boot application with jwt to asymmetric encryption with private and public key.
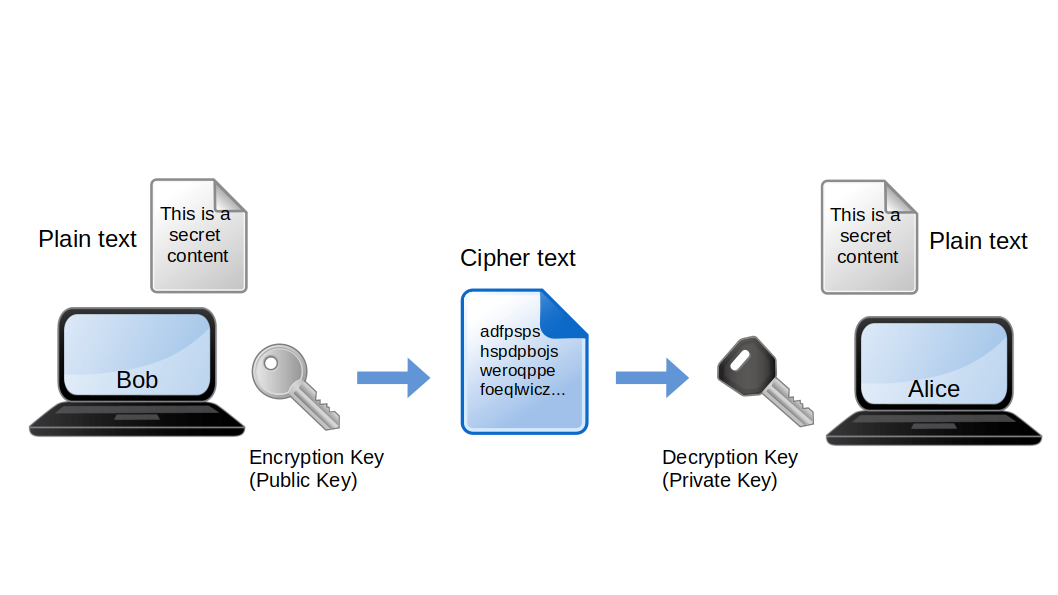
Asymmetric Encryption 2d Garden 1) does the asymmetric signing of jwt tokens support the issuing of refresh tokens? 2) why my authorization server is not issuing a refresh token based on the below configuration? @override. public void configure(authorizationserverendpointsconfigurer endpoints) throws exception { tokenenhancerchain chain=new tokenenhancerchain();. Learn how to convert a spring boot application with jwt to asymmetric encryption with private and public key. Json web tokens (jwt) have become a popular method for securing spring boot applications. in this article, we’ll explore the differences between symmetric and asymmetric jwt implementations in. Asymmetric encryption is more computationally intensive than symmetric — so you may find that asymmetric encryption techniques will embed a dynamically generated symmetric key used to encrypt a majority of the payload within a smaller area of the payload that is encrypted with the asymmetric key. Learn how to develop an authentication mechanism for spring security with the metamask extension using asymmetric encryption and providing data privacy. join the dzone community and get the. For symmetric encryption, you’ll define a secret key. for asymmetric encryption, you can specify paths to public and private keys. the juwatech.encrypt.key is used for aes symmetric.

Java Spring Boot Application With Asymmetric Encryption Json web tokens (jwt) have become a popular method for securing spring boot applications. in this article, we’ll explore the differences between symmetric and asymmetric jwt implementations in. Asymmetric encryption is more computationally intensive than symmetric — so you may find that asymmetric encryption techniques will embed a dynamically generated symmetric key used to encrypt a majority of the payload within a smaller area of the payload that is encrypted with the asymmetric key. Learn how to develop an authentication mechanism for spring security with the metamask extension using asymmetric encryption and providing data privacy. join the dzone community and get the. For symmetric encryption, you’ll define a secret key. for asymmetric encryption, you can specify paths to public and private keys. the juwatech.encrypt.key is used for aes symmetric.