
The Slam Method For Fighting Phishing Etactics Slam is an acronym that helps remind you of what to look for when it comes to possible phishing emails. when you are able to easily identify these threats, your likelihood of costing your company (or even you personally) financial loss is greatly diminished. By applying the slam method, you can reduce the risk of falling victim to phishing emails. regular training on detecting such attacks and implementing basic security measures would ensure that employees and organizations stay one step ahead of these attacks.

The Slam Method For Fighting Phishing Etactics The slam method offers a simple yet effective strategy for combating phishing by encouraging users to scrutinize emails for common red flags—sender, links, attachments, and messages. Slam method stands for: stop, look, ask, and manage. the method is four step framework that involves double checking the sender, link, attachment, and message. The slam method in security is a simple checklist to spot phishing emails by checking the sender, links, attachments, and message for red flags. it helps users avoid clicking on malicious links or opening harmful files, protecting against data breaches. Phishing attacks use urgent communication from disguised senders to steal your information. learn how the slam method can stop these cybercriminals.
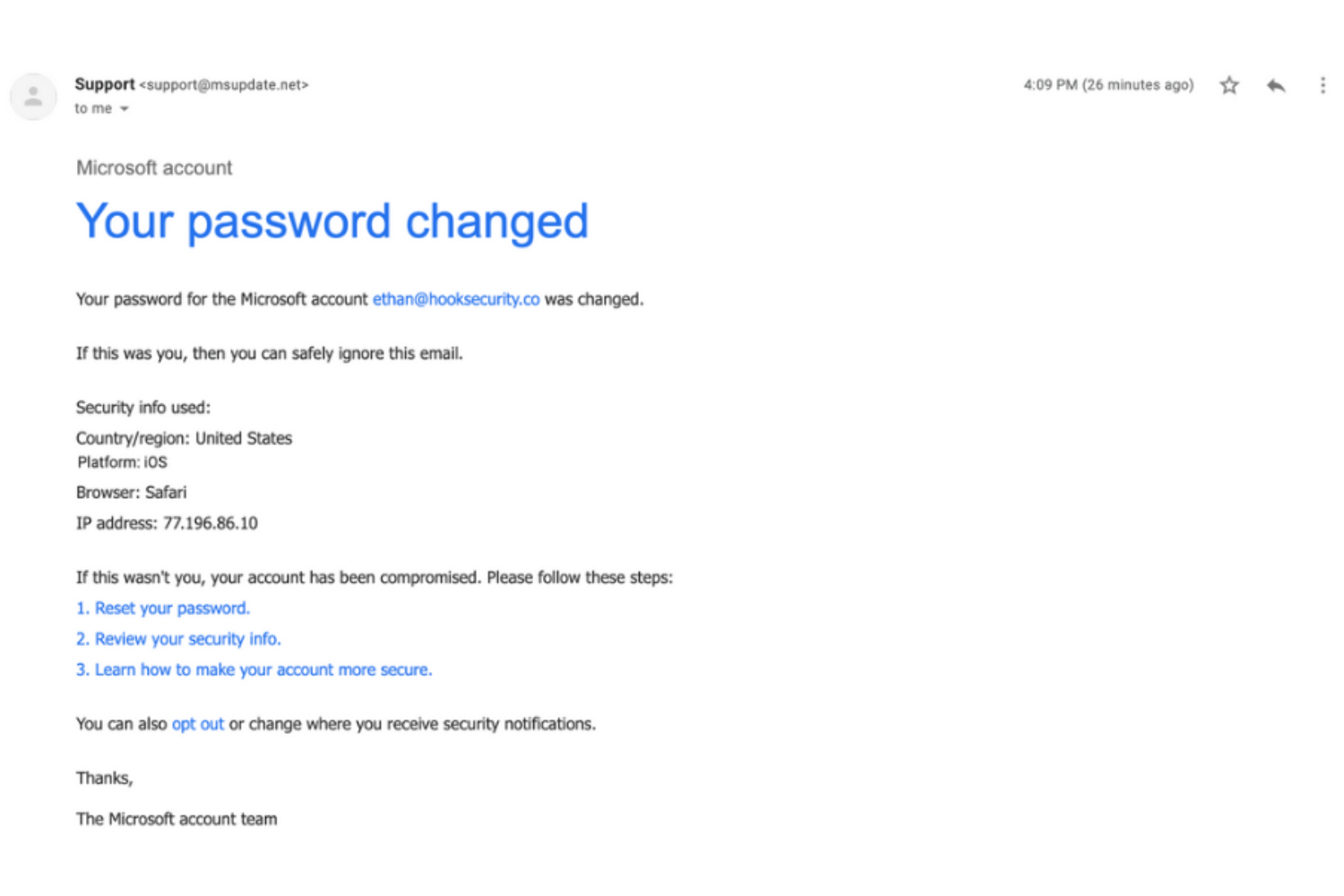
The Slam Method For Fighting Phishing Etactics The slam method in security is a simple checklist to spot phishing emails by checking the sender, links, attachments, and message for red flags. it helps users avoid clicking on malicious links or opening harmful files, protecting against data breaches. Phishing attacks use urgent communication from disguised senders to steal your information. learn how the slam method can stop these cybercriminals. Slam is an acronym for four key areas of an email message to check before trusting it. these are: s = sender l = links a = attachments m = message text by giving people the term “slam” to use, it’s quicker for them to check suspicious email. this device helps them avoid missing something important. all they need to do use the cues in the. Creating internal simulations of phishing scams is a good strategy to help users avoid falling victim to phishing attacks. through simulated phishing campaigns, clinic staff members are exposed to real life examples of phishing attacks so they can better spot phishing emails. A short and sweet explanation of what slam is and how you can protect your business from phishing attacks when you use the slam method. An effective defense against falling victim to phishing attacks is adopting the slam method. it's a quick, four step checklist that encourages users to briefly pause and examine potentially.

The Slam Method For Fighting Phishing Etactics Slam is an acronym for four key areas of an email message to check before trusting it. these are: s = sender l = links a = attachments m = message text by giving people the term “slam” to use, it’s quicker for them to check suspicious email. this device helps them avoid missing something important. all they need to do use the cues in the. Creating internal simulations of phishing scams is a good strategy to help users avoid falling victim to phishing attacks. through simulated phishing campaigns, clinic staff members are exposed to real life examples of phishing attacks so they can better spot phishing emails. A short and sweet explanation of what slam is and how you can protect your business from phishing attacks when you use the slam method. An effective defense against falling victim to phishing attacks is adopting the slam method. it's a quick, four step checklist that encourages users to briefly pause and examine potentially.