
Understanding A Phishing Attack The cybercriminal group has broadened its attack scope across several new industries, bringing valid credentials to bear on help desks before leveraging its new learnings of cloud intrusion tradecraft Specific examples of Scattered Spider’s social engineering tactics include “impersonating employees or contractors to deceive IT help desks into granting access,” or “convincing help desk services to
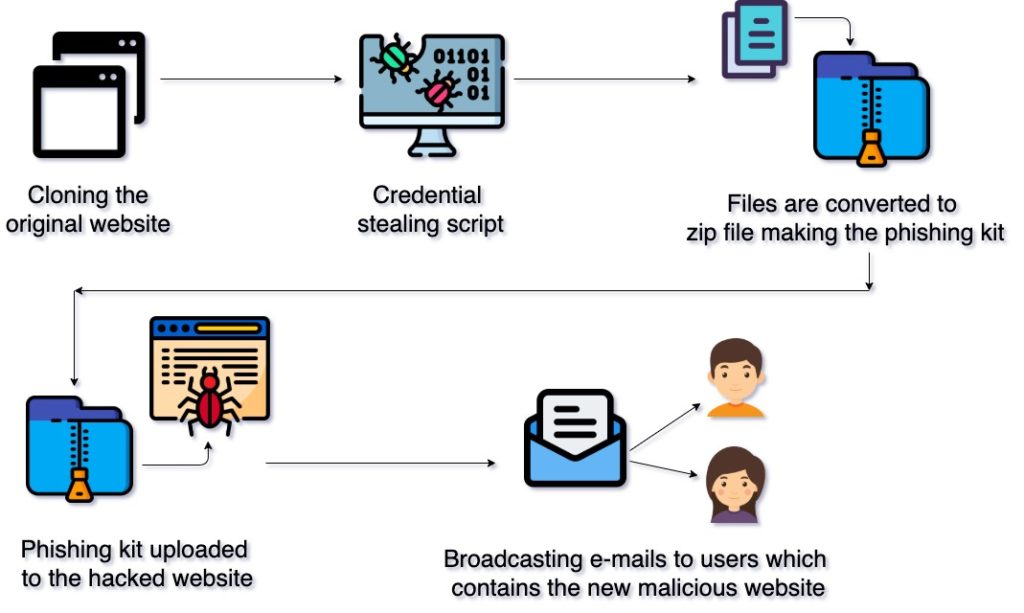
Understanding A Phishing Attack A new Nim-based malware campaign targets macOS users in crypto and Web3 firms, using novel persistence tricks and encrypted communication 66% of hotel IT and security executives expect a rise in attack frequency and 50% an increase in severity during the summer 2025 travel season, according to new research released today by VikingCloud A new FileFix attack allows executing malicious scripts while bypassing the Mark of the Web (MoTW) protection in Windows by exploiting how browsers handle saved HTML webpages Image courtesy by QUEcom The recent data breach at Ahold Delhaize has sent shockwaves through the business community, highlighting

Understanding A Phishing Attack A new FileFix attack allows executing malicious scripts while bypassing the Mark of the Web (MoTW) protection in Windows by exploiting how browsers handle saved HTML webpages Image courtesy by QUEcom The recent data breach at Ahold Delhaize has sent shockwaves through the business community, highlighting New computer viruses in 2025 are more complex and target specific industries, like online stores and healthcare AI is being used by bad guys to make new computer viruses and attacks faster and harder Clickjacking tricks unsuspecting people into clicking on links they think are harmless — but then downloads malware, harvests login credentials, and takes over online accounts A recent ruling by the Dresden Higher Regional Court is making waves Despite a bank customer's gross negligence in a phishing scam, the savings bank must reimburse part of the loss The reason: The Dataquest features, A 16B password leak exposes the cracks in global cybersecurity Experts call for zero-trust, quantum-safe encryption, and passwordless systems

Understanding A Phishing Attack New computer viruses in 2025 are more complex and target specific industries, like online stores and healthcare AI is being used by bad guys to make new computer viruses and attacks faster and harder Clickjacking tricks unsuspecting people into clicking on links they think are harmless — but then downloads malware, harvests login credentials, and takes over online accounts A recent ruling by the Dresden Higher Regional Court is making waves Despite a bank customer's gross negligence in a phishing scam, the savings bank must reimburse part of the loss The reason: The Dataquest features, A 16B password leak exposes the cracks in global cybersecurity Experts call for zero-trust, quantum-safe encryption, and passwordless systems

Understanding A Phishing Attack A recent ruling by the Dresden Higher Regional Court is making waves Despite a bank customer's gross negligence in a phishing scam, the savings bank must reimburse part of the loss The reason: The Dataquest features, A 16B password leak exposes the cracks in global cybersecurity Experts call for zero-trust, quantum-safe encryption, and passwordless systems
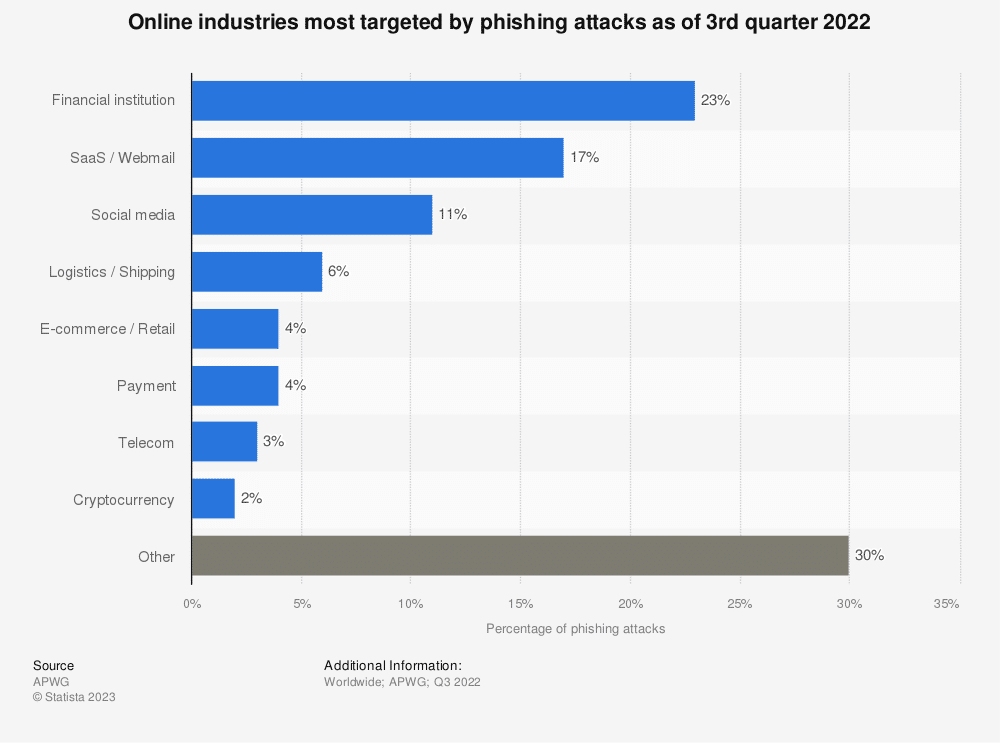
Understanding A Phishing Attack