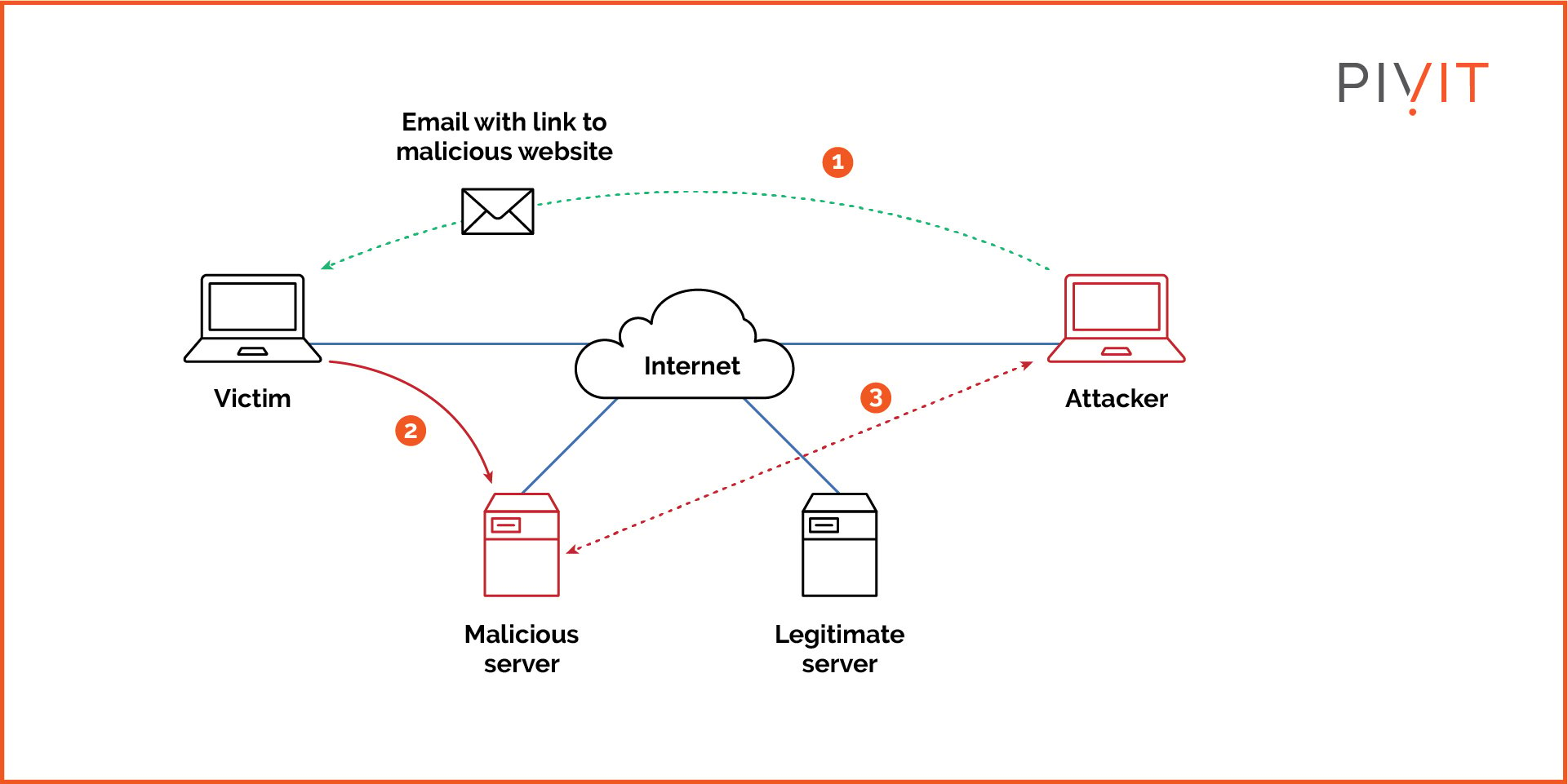
Phishing Attack Overview Phishing is a form of social engineering and a scam where attackers deceive people into revealing sensitive information [1] or installing malware such as viruses, worms, adware, or ransomware. Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.

What Is Phishing Attack How It Works Definition What is phishing? phishing is a type of cyber attack where cybercriminals attack you through social engineering, which involves deceptive communications designed to gain trust or elicit fear. these deceptive attacks can happen through e mail, text message, or even voice calls. Scammers use email or text messages to trick you into giving them your personal and financial information. but there are several ways to protect yourself. scammers use email or text messages to try to steal your passwords, account numbers, or social security numbers. Phishing is a type of cyberattack designed to deceive people into revealing sensitive information. learn how to prevent phishing from harming your organization. Phishing is a social engineering cyberthreat where scammers impersonate a trustworthy source and trick you into revealing sensitive data like passwords, credit card numbers, or personally identifiable information.

What Is Phishing Learn How This Attack Works 2025 Threatshub Phishing is a type of cyberattack designed to deceive people into revealing sensitive information. learn how to prevent phishing from harming your organization. Phishing is a social engineering cyberthreat where scammers impersonate a trustworthy source and trick you into revealing sensitive data like passwords, credit card numbers, or personally identifiable information. Phishing attempts are fraudulent activities where scammers use email or text messages aiming to trick individuals into revealing sensitive information like passwords, bank account numbers, or social security numbers. recognizing phishing can be achieved by being alert to certain red flags. Spoofing and phishing are key parts of business email compromise scams. spoofing is when someone disguises an email address, sender name, phone number, or website url—often just by changing one. How to prevent successful phishing attacks email filtering and anti phishing software implement advanced anti phishing filters that scan incoming emails for suspicious attachments, malicious links, or sender spoofing attempts. Phishing is a form of online fraud in which hackers attempt to get your private information such as passwords, credit cards, or bank account data. this is usually done by sending false emails or messages that appear to be from trusted sources like banks or well known websites.
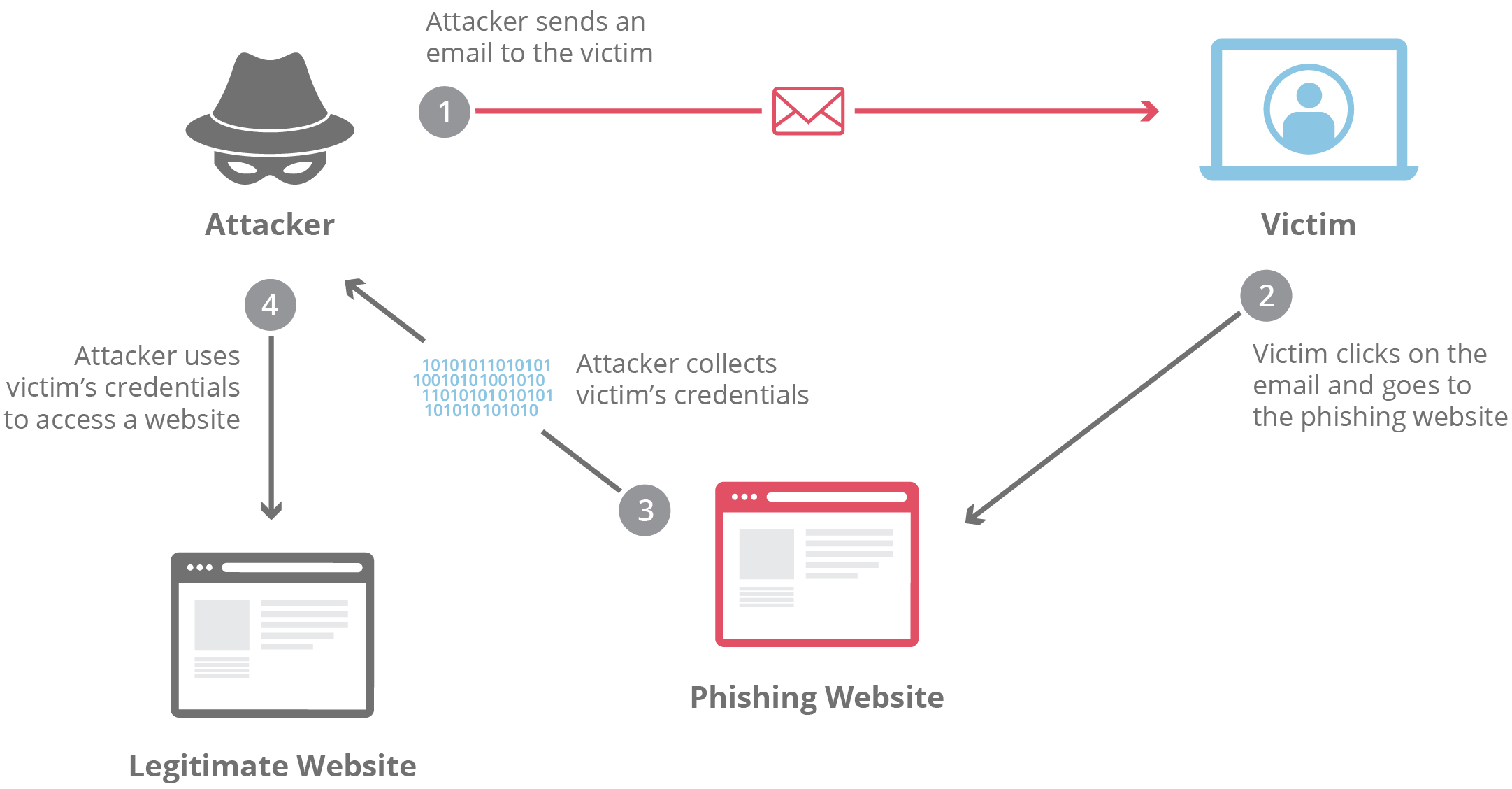
Phishing Attack 3 Real Phishing Attacks Your C Suite Needs To See Phishing attempts are fraudulent activities where scammers use email or text messages aiming to trick individuals into revealing sensitive information like passwords, bank account numbers, or social security numbers. recognizing phishing can be achieved by being alert to certain red flags. Spoofing and phishing are key parts of business email compromise scams. spoofing is when someone disguises an email address, sender name, phone number, or website url—often just by changing one. How to prevent successful phishing attacks email filtering and anti phishing software implement advanced anti phishing filters that scan incoming emails for suspicious attachments, malicious links, or sender spoofing attempts. Phishing is a form of online fraud in which hackers attempt to get your private information such as passwords, credit cards, or bank account data. this is usually done by sending false emails or messages that appear to be from trusted sources like banks or well known websites.