
An Efficient Data Security In Cloudcomputing Using The Rsa Encryption This article describes best practices for data security and encryption. the best practices are based on a consensus of opinion, and they work with current azure platform capabilities and feature sets. How does cloud encryption work? encryption leverages advanced algorithms to encode the data, making it meaningless to any user who does not have the key. authorized users leverage the key to decode the data, transforming the concealed information back into a readable format.
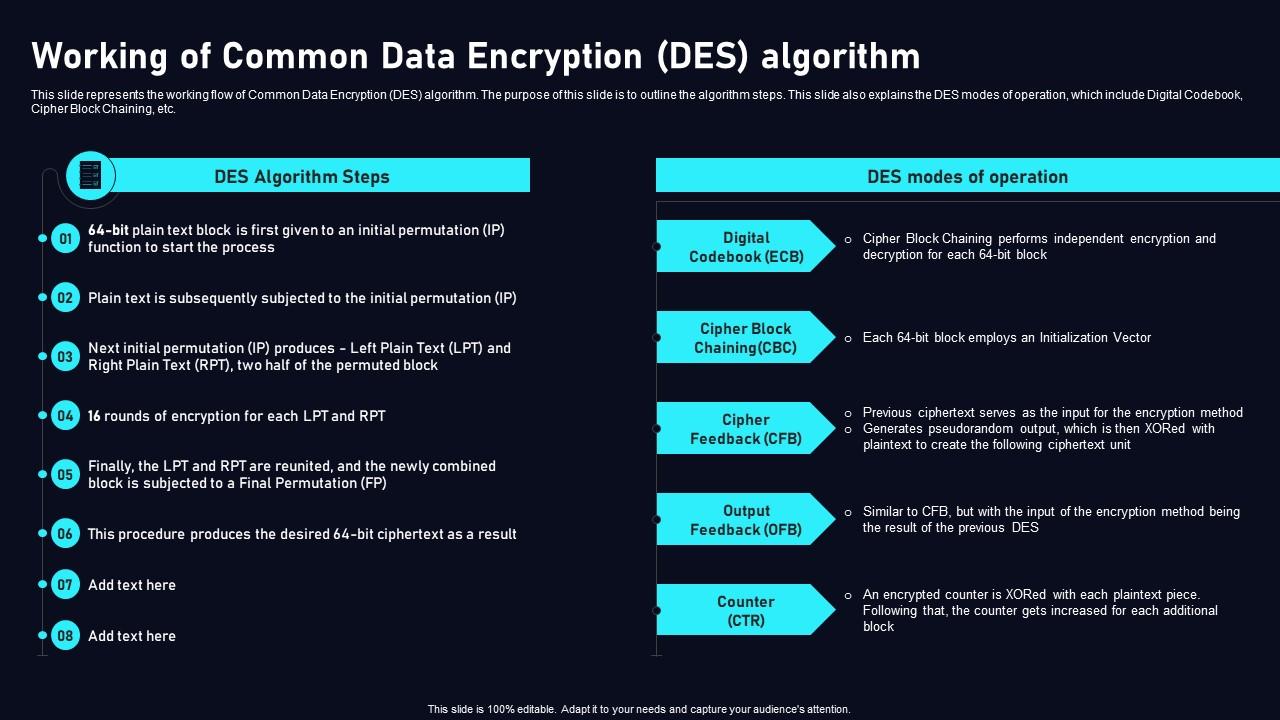
Working Of Common Data Encryption Cloud Data Security Using Cloud encryption refers to the process of encoding data into an indecipherable format before storage in cloud environments. access requires appropriate decryption keys, ensuring information remains protected. Cloud encryption transforms plaintext data into data that is completely indecipherable (called ciphertext). this means if a cybercriminal manages to hack into your email or web traffic, what they’re left with is useless to them. they have the data, but not the key that would turn the gibberish back into usable information. Explore key strategies to secure your data in the cloud against emerging threats. in today’s cloud centric world, data security is paramount. our comprehensive guide explores the intricacies of cloud encryption, arming you with the knowledge to protect your sensitive information from prying eyes. Cloud encryption safeguards data from misuse and solves additional critical security challenges. these include: adherence to regulatory standards for data protection and privacy. improved security against illegal data access by other public cloud tenants.

Data Security In Cloud Computing Pdf Cloud Computing Information Explore key strategies to secure your data in the cloud against emerging threats. in today’s cloud centric world, data security is paramount. our comprehensive guide explores the intricacies of cloud encryption, arming you with the knowledge to protect your sensitive information from prying eyes. Cloud encryption safeguards data from misuse and solves additional critical security challenges. these include: adherence to regulatory standards for data protection and privacy. improved security against illegal data access by other public cloud tenants. Encryption is a critical component of cloud security. it involves encoding data in such a way that only authorized users can access it. implementing encryption for data in transit and data at rest can help protect sensitive data from unauthorized access and data breaches. Data security in cloud computing is a shared responsibility that requires a proactive and comprehensive approach. by understanding the challenges, implementing the best practices outlined in this guide, and staying informed about the latest threats, you can confidently secure your data in the cloud and unlock the full potential of this. Cloud encryption is the process of encoding and transforming data before transferring it to the cloud. this process converts plaintext data into ciphertext using mathematical algorithms and makes the data unreadable, thus protecting it from unauthorized and potentially malicious users. Risk management in cloud computing hinges on comprehensive measures to prevent data breaches and compliance violations. let’s dive into the essential technologies, policies, and practices for cloud data security.

Data Security Of Cloud In Cloud Computing Pdf Encryption is a critical component of cloud security. it involves encoding data in such a way that only authorized users can access it. implementing encryption for data in transit and data at rest can help protect sensitive data from unauthorized access and data breaches. Data security in cloud computing is a shared responsibility that requires a proactive and comprehensive approach. by understanding the challenges, implementing the best practices outlined in this guide, and staying informed about the latest threats, you can confidently secure your data in the cloud and unlock the full potential of this. Cloud encryption is the process of encoding and transforming data before transferring it to the cloud. this process converts plaintext data into ciphertext using mathematical algorithms and makes the data unreadable, thus protecting it from unauthorized and potentially malicious users. Risk management in cloud computing hinges on comprehensive measures to prevent data breaches and compliance violations. let’s dive into the essential technologies, policies, and practices for cloud data security.

Common Data Encryption Des Cloud Data Security Using Cryptography Cloud encryption is the process of encoding and transforming data before transferring it to the cloud. this process converts plaintext data into ciphertext using mathematical algorithms and makes the data unreadable, thus protecting it from unauthorized and potentially malicious users. Risk management in cloud computing hinges on comprehensive measures to prevent data breaches and compliance violations. let’s dive into the essential technologies, policies, and practices for cloud data security.

Pdf Enhancing Cloud Data Security Using Multilevel Encryption